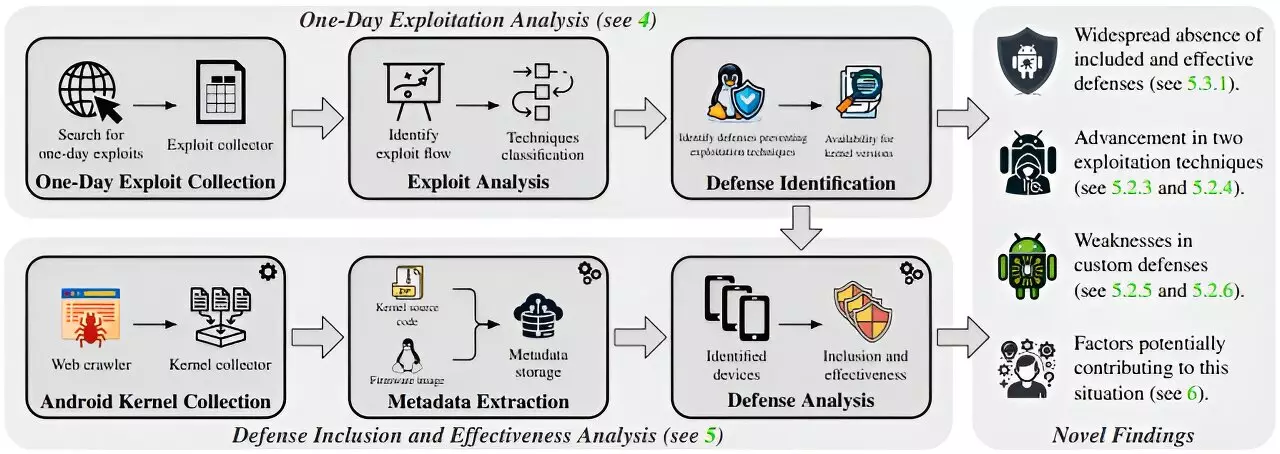
As smartphones have become integral to daily life, the expectations for their security have intensified. We rely on these devices for not just communication but also for managing sensitive information such as financial data, personal schedules, and official documents. Given these increasing demands, a comprehensive understanding of the threats facing smartphone users is essential. Recent research conducted by a team from Graz University of Technology (TU Graz) brings to light critical vulnerabilities in the Android kernels of some of the most prominent smartphone manufacturers. Their findings raise crucial questions about the adequacy of existing security measures in protecting users against potential cyber threats.
The study, presented at the Usenix Security Symposium, highlighted alarming shortcomings in how various manufacturers implement security for their devices. Evaluating devices from ten leading firms, the researchers found that only a slim percentage—between 29% and 55%—of the smartphones tested could effectively guard against known exploits, also referred to as one-day exploits. In stark contrast, Google’s Generic Kernel Image (GKI) version 6.1 exhibited a significantly improved protective capacity, capable of thwarting around 85% of these attacks. The disparity in effectiveness points to a systemic issue within manufacturer kernels, which were found to be up to 4.6 times less secure than Google’s standardized approach.
The researchers also delved into the variations between different Android versions and kernel types utilized by manufacturers between 2018 and 2023. The kernel version spectrum ranged from 3.10 to 6.1, with older versions inherently offering less robust security. Surprisingly, it was discovered that even an older kernel like version 3.1 could outshine approximately 38% of current configurations offered by manufacturers, provided it had activated security measures. This finding indicates a critical misalignment between available security technology and its implementation by smartphone manufacturers, underscoring a significant gap in protective measures that should be prioritized.
An additional aspect of the analysis revealed a worrying trend regarding low-end smartphone models. The research indicated these budget devices were about 24% more vulnerable to attacks compared to their high-end counterparts. The reasoning is both technical and financial; manufacturers often disable security features to conserve processing power and memory in less expensive devices, consequently compromising user safety. This trade-off raises ethical concerns about the responsibilities of manufacturers to prioritize user security, regardless of device price.
In light of these findings, the researchers at TU Graz are optimistic that their results will push manufacturers to enhance security protocols within their kernels moving forward. Notably, several companies, including Motorola, Huawei, and Samsung, have acknowledged the study’s insights and begun to implement patches as a reaction to the vulnerabilities highlighted. Further, the researchers have urged Google to reassess the Android Compatibility Definition Document (CDD), which delineates the requirements for devices to be considered compatible with Android. This update could potentially ripple through the industry, improving overall security standards across all manufacturers.
The vulnerabilities identified in the Android kernels serve as a wake-up call for both manufacturers and users. As smartphones continue to incorporate essential functionalities that demand robust security, there is no room for complacency in software development and implementation practices. Only through a commitment to enhanced protective measures, rigorous testing, and the active collaboration between researchers and manufacturers can we hope to build a more secure framework for mobile technology. As Lukas Maar and his colleagues advocate, the path forward requires not only awareness of these vulnerabilities but also strategic action to fortify the defenses that keep users safe in an increasingly digital world.